Supply Chain Attacks and Cyberinsurance
The rise in sophisticated supply chain cyberattacks doesn’t just affect enterprises; there are also impacts on the insurance industry and on enterprises’ cyberinsurance costs.
What is a software supply chain attack?
Software supply chain attacks are cyberattacks against an organization’s software supply chain infrastructure and process. In such attacks, the attacker gains access to a company’s software supply chain through a misconfiguration, vulnerability or manipulation of the supply chain tools or supporting services, and they use this access to steal data, tamper with the application or commit an unauthorized modification of software while it is being delivered. At this point, the attackers can use the company’s software update as a vehicle to distribute malicious code or create backdoors in the company’s customers’ environments.
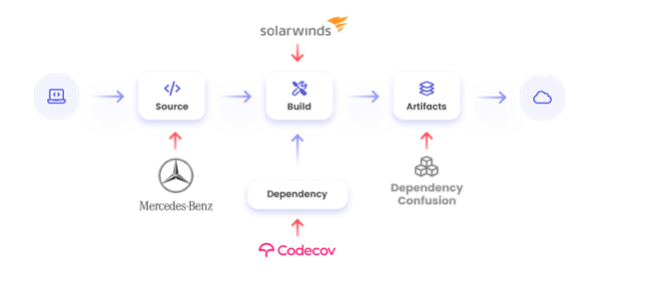
The SolarWinds attack in late 2020 is a good example of the potential damage that can be caused by a single software supply chain attack. In this nation-state attack against the networking tools’ vendor SolarWinds, about 18,000 customer environments were exposed and as many of 100 organizations were affected by it, including U.S. government agencies and top enterprises such as Microsoft, FireEye and more.
Understanding Software Supply Chain Risks
Over the past few years, software companies have adopted continuous integration and delivery (CI/CD) processes to automate their software supply chain, allowing them to expedite their products and feature releases and maintain a competitive advantage over their markets.
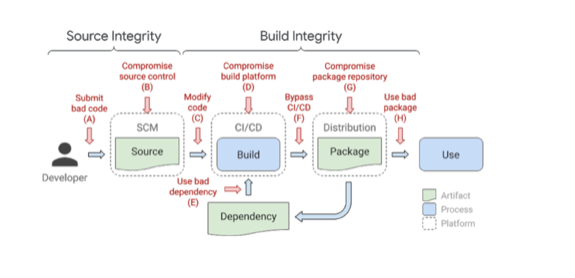
The supply chain tools that form part of these modern development processes are open by design, automated, collaborative in nature and connected to many supporting systems, which creates an environment that is extremely complex and hard to secure. A popular model that illustrates the software supply chain threats is Google SLSA. This model provides high-level guidelines for protecting your software development process.
Supply Chain Threats: Google SLSA Model
These types of attacks have been on the rise in recent years and are proving to be a common and reliable way to attack software companies, as seen in the cases of SolarWinds, Codecov and Microsoft.
By targeting big-name companies and compromising their commonly used software, the attackers gain access to all the downstream organizations that are making use of that software; in many cases, victims may be unaware that they’re deploying these backdoors.
The Impact on Cyberinsurance
All technology vendors are vulnerable to software supply chain attacks—any company that produces software for other organizations is a potential target. Threat actors have deep resources and the skills to penetrate even security-conscious firms.
The role of cyberinsurance is to protect organizations against the costs of cybercrime and digital threats. It covers organizations from risks that include first-party losses such as business interruption, restoration and crisis communications, as well as third-party losses such as data breaches, network interruption, breach notification expenses and more, with the aim of protecting companies from significant financial losses as a result of cyberattacks.
The recent wave of software supply chain attacks is changing the paradigm for insurance companies by introducing a new type of attack that can affect thousands of businesses at once, with combined damage of tens of millions of dollars. According to cybersecurity risk vendor BitSight, an attack such as SolarWinds will likely cost cyberinsurers around US$90 million.
Software Supply Chain Attack Vectors
The Cyberinsurers Dilemma: Ransomware
In the past two years, major cyberinsurers have suffered significant losses from ransomware attacks, as payouts were much higher than originally expected. The damage from ransomware has gotten so severed that some cyberinsurers are stepping away from covering it. AXA France, for example, announced that they will not reimburse ransomware payments for new policy-holders in France. It’s become clear from the unexpected response to the latest ransomware attacks that the cyberinsurance industry didn’t take into account the vast impact of ransomware and supply chain attacks and were not prepared for the number of companies claiming losses against these policies.
“High-profile cyber events involving critical vendors for a host of businesses have cyber insurers rethinking their strategy going forward in the beginning of 2021. Insurers are now demanding higher cybersecurity standards before deploying capacity and cutting back capacity significantly,” said Shay Simkin, global head of cyber at Howden Insurance Brokers. “According to research in the U.S., supply chain attacks had risen by 42% in the first quarter of 2021 and the impact on insurance buy is across the board. Underwriters can cherry-pick clients and the challenge for us brokers now is one of securing coverage at an affordable premium.”
The recent supply chain attack against Kaseya VSA, a patch management and monitoring platform used by MSPs, spread REvil ransomware to over 1,000 companies; attackers asked for $50 million. This is an example of the massive damage that can be caused by using a software supply chain attack to distribute ransomware.
REvil Ransomware Hits 1,000+ Companies in MSP Supply Chain Attack
“Technology will continue to be critical to enable connectivity and accessibility and I believe that we will see more supply chain attacks like Kaseya,” said Simkin. “The supply chain risk must be managed through new specialized products and focused risk management of vendors.”
A Glimpse of the Future
The insurance industry is feeling the pressure from the surge in large-scale cyberattacks. The recent supply chain attacks show there is still work to be done.
“The increase in software supply chain attacks as a way to breach thousands of customers at once, both in terms of the frequency of attacks and the severity of damage, will force cyberinsurers to adapt their underwriting strategies,” said Simkin. “Just like we saw almost every insurer introduce some type of ransomware limitation, we can expect the same type of adjustments to their policies to cover supply chain attacks.”
When it comes to ransomware, once insurers better understood the impact of these cyberattacks and began taking into account how companies manage their security posture and preparedness, it is logical to assume that they will extend these practices to cover (or not cover, as the case may be) supply chain attacks as well. Ultimately, insurance companies are in the business of making money, so we should expect new requirements added to cybersecurity policies and changes to the pricing structure to protect themselves. We expect that software companies will be required to implement software supply chain security controls as part of their overall security strategy to be eligible for cyberinsurance coverage and payments in case of an attack.